
The problem behind mobile Tor browsers' IP disclosure
As shown in the previous article from the end of May, nearly all mobile "private" Tor browsers leak the IP address under normal circumstances. The first problem occurs because of external multimedia elements which are loaded by the internal multimedia players. Finally, this can be used to determine the 'real' network IP of an user by anyone that has access to the raw http stream.
| Browser | HTML5 Multimedia Leak | Download-related Leak | unique HTTP header |
|
| Android | Orweb: Private Web Browser | X | at least 0.6 (update) |
X |
| Anonymous Browser Connect TOR | X | X | X | |
| Firefox Add-On | ok (*) | internal: ok | X | |
| iOS | Onion Browser | standard: yes (fixed in 1.5.3) |
standard: yes (fixed in 1.5.3) |
X |
| Red Onion | standard: yes (fixed in 1.8) |
standard: yes (fixed in 1.8) |
overwritable |
With the use of autoplay no user interaction is needed to get a HTTP and DNS request outside the (SOCKS) Tor proxy. Normally these requests are then performed over your normal connection. This is what never should have happened - the real IP address gets visible due to a webpage requested via Tor having video elements on it.
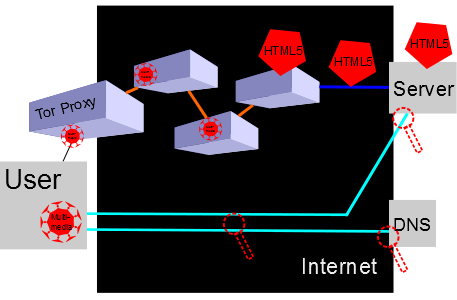
The multimedia content triggers a normal DNS and HTTP request.
Proof of concept
The code below simply includes a video url which is then accessed by the corresponding multimedia player. During the check the IP requesting this resource is displayed back to the user.
Originally, my old Android phone did also perform the poster-image request outside Tor. Now only the source file is handled. However, the poster tag is still needed to get autoplay working (API level? Why? :) I am not sure if this holds for other versions of Android.
<video controls="controls" autoplay="autoplay" poster="<=php file>"> <source src="<=php file>" type="video/mp4" /> </video>
Insertion of this code leads to one or two requests being performed outside Tor.
HTLM5 Video IP Leakage:
→ perform your own check of your mobile Tor browser.
Android
The stagefright player handles the multimedia content on Android. It is required to set a WebChromeClient for inline HTML5 Video.
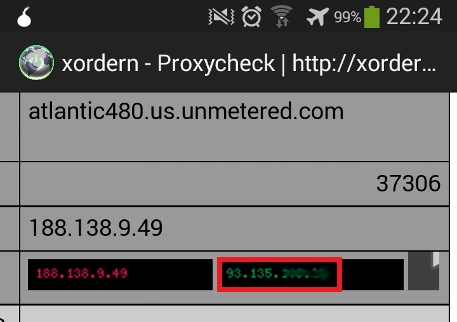
Orweb: real IP discovery with HTML5 multimedia element (right)
The requests of the stagefright player are performed outside the SOCKS proxy (Orbot) with a different user-agent string. It is either empty or stagefright/1.2 (Linux;Android 4.3), but might also be called HTC Streaming Player for an HTC One.
The normal user-agent of Orweb is Mozilla/5.0 (Windows NT 6.1; rv:10.0) Gecko/20100101 Firefox/10.0
The anonymous browser used Mozilla/5.0 (Linux; U; Android 4.3; de-de; GT-I9300 Build/JSS15J) AppleWebKit/534.30 (KHTML, like Gecko) Version/4.0 Mobile Safari/534.30 for the Tor requests.
iOS
On iOS the standard user-agent of Onion Browser is (over Tor):
OnionBrowser/20140520.1 CFNetwork/672.1.14 Darwin/14.0.0
while the media requests are performed with this ua and real IP:
AppleCoreMedia/1.0.0.11D201 (iPad; U; CPU OS 7_1_1 like Mac OS X; de_de)
(Media-)Download related issue
The second problem is related to the handling of external links to e.g. video files. The iOS browser may start the 'internal core player' that handles the requests outside Tor. The Anonymous Browser seems to download it directly with the AndroidDownloadManager (without any question). And Orweb performs an internal proxying but finally a request is done over the normal connection.
This can be checked with an extended check.
Orweb: Apache-HttpClient/UNAVAILABLE (java 1.5)
Anonymous Browser (connecttor): AndroidDownloadManager/4.3 (Linux; U; Android 4.3; GT-I9300 Build/JSS15J)
Onion Browser: AppleCoreMedia/1.0.0.11D201 (iPhone; U; CPU OS 7_1_1 like Mac OS X; en_us)
These user-agents were used for the download with the real IP.
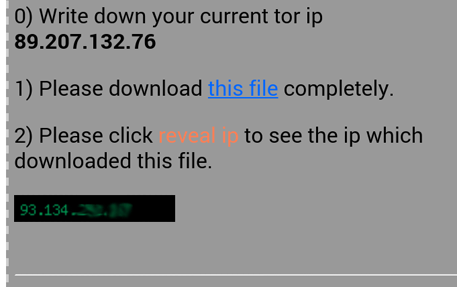
Downloads being performed without Tor - extended check
Solutions
The best recommendation is not to use a mobile plattform if you desire strong security. Otherwise, a solution for the Onion Browser is to set a special option which blocks all active elements. Unfortunately, it is disabled by default and these elements won't work anymore.
Orweb on Android is still unfixed. There is a workaround by using transparent proxying for this app (works only for rooted phones). Another solution is to use the Firefox for Android Add-On 'proxy mobile' which is also provided by the authors of Orweb. In October 2013 a new project (called Orfox) was started but isn't finished yet.
The Onion Browser offers the possibility to "Block All Active Content". Unfortunately, it is disabled by default. More information.
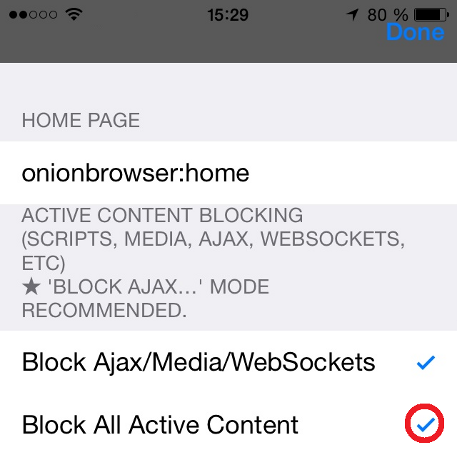
Onion Browser Settings: You can block All Active Content to avoid the discovery.
Conclusion
Now everything is fine? No! The IP discovery vulnerability is still unfixed and users are not really notified. But even if they were, all of the browsers would show a very unique behavior and http headers. For example the Firefox Add-On solution is not as secure as using e.g. the Tor Browser Bundle because the plugin does not change many settings. Therefore, at least the HTTP_ACCEPT_LANGUAGE might contain the languages being set on the device which might be very unique.
Firefox with proxy mobile add-on (June 28th, 2014):
HTTP_ACCEPT_LANGUAGE: de,en-US;q=0.7,en;q=0.3
Another privacy critical behaviour is the "Anonymous Browser Connect TOR" performing a test during the start-up. It asks for the location of the real IP and the Tor IP - at almost the same moment. The test is performed via http requests (http://evda-connector.appspot.com/torvalidator) and the fact which Tor IP is used can be connected by a simple cross-correlation in time domain.
* de=Deutsch = German
UPDATE 2 (October 21st, 2014) :
The app Red Browser Red Onion is vulnerable to IP leakage issues, too. This wasn't mentioned in the article until now. You can disable all active content by setting "Block All (Better Security)" in the settings.
Please keep in mind that most of these mobile browsers have address bar spoofing issues with activated Javascript. Check the test cases on ios.browsr-tests.com (external).
UPDATE (July 3rd, 2014) :
A new more accurate manual test has been published. Try it if you think your configuration might be affected by the HTML5 multimedia leak but the original check only displays your Tor IP. The original check relies on videos being started automatically (e.g. Android 4.4.4 does not autoplay) but it does not need any user interaction nor javascript.
In addition, Orweb 0.5.2 might not be vulnerable to the download issue because it crashes before it downloads any file.
app specific update:
-> Firefox Add-On / ProxyMob: In case of using Firefox with Addon be sure to disable Javascript or at least e.g. WebRTC (about:config -> media.peerconnection.enabled: false) in order to avoid IP disclosures on different ways (external demo page).
-> Red Onion (Jan 22nd, 2015): The version 1.8 seems to fix this issue. When accessing a media content you have to 'tap' and select an appropriate option how to handle it.
-> Onion Browser (July 2nd, 2014): Version 1.5.3 fixes the standard "Block Media" filtering to address the IP leakage. Thanks.
-> Orweb (June 30th, 2014): Comment on this article. The download issue got fixed in repository. Not yet published to the App Store.
The tests on Android were mostly performed with "Orweb 0.6" (F-Droid) and "Anonymous Browser Version 1.10" on Android 4.3.
A change in the spelling of Tor was made because sometimes it was called TOR which is in fact useful to distinguish between the German translation and the Tor Project.