
Why you really shouldn't use Orweb anymore... - WHAT HAPPENED?
See the newest article on mobile Tor browsers from June 28th for more information about the IP leakage problem.
| Notified. | 07/29/2013 |
| Request 1. | 08/03/2013 |
| Request 2. | 08/12/2013 |
| Confirmed. | 08/12/2013 |
| Bug tracker item. | 08/20/2013 |
| Blog post. | 08/21/2013 |
| Still unfixed in PlayStore. | 06/01/2014 |
In times where spying operations become more and more public, people are interested in protecting their data against analysis – either from huge companies or from some governments. One way to do this would be to use Tor, maybe also on the smartphone. The tool Orbot, which is available for Android, is a Tor proxy to allow applications to connect through the Tor network.
A browser which is fully compatible with Orbot is the Orweb: Private Web Browser. Unfortunately, it has one really strange security flaw. Anyone who has access to the raw html traffic ( especially website owners and, at least for unprotected connections, as well the operator of the exit node and the people inbetween) could modify the server response in order to get the real ip of the user.
Description of Orweb
After the bug showed up in the bug tracker, a blog post was released immendiately but no change was made to the official releases available from the Google PlayStore. The problem is the behaviour of the internal browser view. It is based on the Android WebView which doesn't handle proxy settings of the internal stagefright player correctly. Therefore, the proxy (Orbot) is ignored for HTML5 video or audio elements. This could help a malicious person to get your actual ip address by inserting specific elements into your traffic. The only exception is if the whole traffic is routed through Tor - what is something I don't recommend, but this is another story.
Orweb security advisory from guardianproject.info
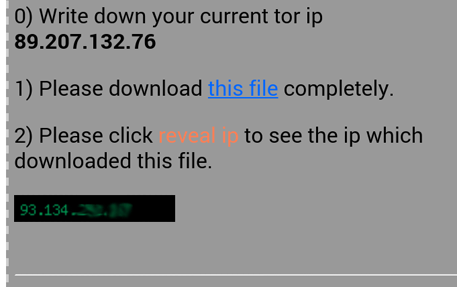
This is what never should have happened - the real ip address is visible on a webpage requested via Tor by only having video elements on it.
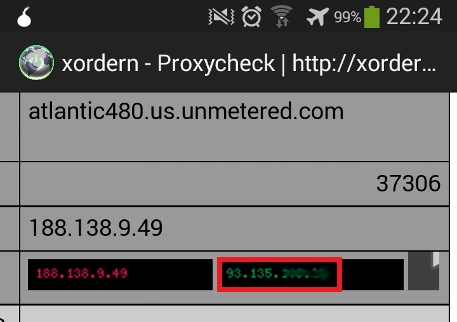
What happened here? - After an additonal check it was clear that it was my real ip.
Unfortunately, the problem is still unfixed. You may perform your own check with the live-test. Please keep in mind that this might expose your real ip over your current connection (which should be performed via Orbot through Tor).
Additional information provided by the PlayStore (up to 5 million installs)
In addition, it has been stated that the problem doesn't exist on all platforms. This might be true but we were still able to reproduce it on at least Android 4.1.2 and 4.3 which might be the platform of several installations.
HTLM5 Video IP Leakage:
→ perform your own check of your ORWEB browser.
Quick solution. Don't use Orweb (– despite it is called the most private and anonymous web browser – ) until this critical issue has been fixed. One alternative might be to use the Firefox for Android Add-On 'proxy mobile' which is also provided by the authors of Orweb and is not affected by this problem. For really "secret" operations you might want to use another device than your personal smartphone.
UPDATE 3 (June 18th, 2014): If you had a rooted smartphone, an alternative solution to address the leak would be setting specificly Orweb for transparent proxying in Orbot. However, this won't help much against other specific http header side information.
| ! ⇒ | The apps 'Connect Tor' (Android) and the 'Onion Browser' (iPhone) are also affected by the same issues as Orweb. The latter had the same problem with enabled HTML5 multimedia elements and it has some issues (1, 2) until now. Please check yourself. |
Second problem occurs via Media Download:
Downloads being performed without Tor - extended check
Some downloads are also performed outside Tor because the browser finally uses the internal Android Download Manager guardianproject.onionkit.trust.StrongHttpsClient
to complete these downloads. Finally, this leads to DNS and HTTP GET requests being performed outside Tor with the user-agent
Apache-HttpClient/UNAVAILABLE (java 1.5).
UPDATE 2 : Android 2.3.5 (Gingerbread) and 4.2 are also vulnerable. I would appreciate some feedback for other versions of Android.
UPDATE (June 1st, 2014) :
On August 21st, 2013 a small commit was published which contains a try to strip out video and audio tags. Nevertheless, it won't fix the issue because <<audio>video would still get a valid <video tag after filtering. Moreover, the tags could be added again with JavaScript if enabled.
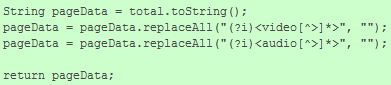
Filtering in removeUnproxyeableElements of
revision 1e9821d6 (08/21/2013) of
Browser.java
Despite this won't work, the function isn't called anymore. This means multimedia tags still bypass the Tor connection on most platforms.
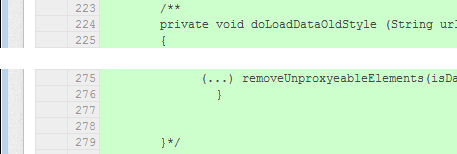
Call commented out in revision 26a8b47e (11/26/2013, diff)
To my knowledge the filtering has never been brought to the PlayStore.
Some paragraphs were renewed to make the problem more clear. Also, a change in the spelling of Tor was made because sometimes it was called TOR which is in fact useful to distinguish between the German translation and the Tor Project.
--------------------
Caution: This information was brought to you by xordern.
See the newest article on mobile Tor browsers from June 28th for more information about the IP leakage problem.